Overview
Your business has chosen MultiLine to manage work numbers which easily integrate into the Microsoft Teams application. This allows you to extend the communication platform you use for internal communications externally.
- Voice integration allows making and receiving calls from Microsoft Teams using the MultiLine work number. This is a real cellular-grade number for superior voice quality whether in the office or on the go.
- Messaging integration allows sending SMS, including group and picture messages, as well as social messages.
This end-to-end guide includes everything you need to get started.
Enabling Voice
To enable voice for your organization, a Microsoft Teams administrator will need to follow these three set-up guides:
- Enterprise Guide: Microsoft Teams Integration - Movius System Configurations 🔒
- Enterprise Guide: Microsoft Teams Integration - Metaswitch Perimeta Licensing and Configurations 🔒
- Enterprise Guide: Microsoft Teams Integration - Licensing and configuration 🔒
After the Microsoft Teams administrator completes set-up, the MultiLine administrator needs to follow this guide:
No action is required by end-users to access Microsoft Teams calling. They make and answer calls in the Teams application as usual.
Enabling Messaging
To enable messaging for your organization, you will need to follow the information in this guide:
End users must install and pin the MultiLine Messaging app to Teams before use.
End User Guides
This Help Center has dedicated sections to Microsoft Teams. It also includes a Teams tab in materials about calling and messaging with MultiLine. The materials are also available in the below guide.
Read on to learn about how to enable Microsoft Teams calling for a user.
Overview
With the MultiLine integration for Microsoft Teams, users can make and receive calls using their MultiLine number directly within the Calls app in Microsoft Teams.
Once enabled by the admin, the user will need to activate the MultiLine i OS or Android mobile app. After activation, the MultiLine number will be added to the Microsoft Teams app.
Incoming call notifications on mobile devices must either be received by the MultiLine app or the Microsoft Teams app. Therefore, we advise admins to disable incoming call notifications for MultiLine mobile apps so that the user receives all incoming call notifications from Microsoft Teams.
Before you start
- Movius must turn on Microsoft Teams for your organization for the feature to be available.
- You must enable Microsoft Teams calling before you can turn off incoming call notifications to the MultiLine app.
- An admin must have "Accounts" Privilege in their Role in the organization to do these instructions. See What Admin Privileges are in Management Portal?.
Enable Microsoft Teams calling for user
MultiLine Administrators enable Microsoft Teams calling for users from the Accounts page. For new users, this is done when adding a user. For current users, this is done by editing the account.
On the accounts page, use the feature toggle to turn MS Teams Calling on.
- When off, a grey x
 will be visible on the toggle and the user will not be able to use Microsoft Teams calling.
will be visible on the toggle and the user will not be able to use Microsoft Teams calling. - When on, a green checkmark
 will be visible on the toggle and the user will be able to use Microsoft Teams calling.
will be visible on the toggle and the user will be able to use Microsoft Teams calling.

Set up Incoming Call Notifications
For best experience, MultiLine and MS Teams cannot both receive incoming call notifications. Therefore, users must either receive incoming calls on MultiLine or on Teams.
Admins can set whether MultiLine will ring on the accounts page. Use the toggle to turn Incoming Call Notifications On MultiLine App off.
- When off, a grey x
 will be visible on the toggle and the user will not receiving incoming call notifications on MultiLine. The user will receive incoming call notifications from Microsoft Teams.
will be visible on the toggle and the user will not receiving incoming call notifications on MultiLine. The user will receive incoming call notifications from Microsoft Teams. - When on, a green checkmark
 the user will receive incoming call notifications on MultiLine. The user will not receive incoming call notifications from Microsoft Teams.
the user will receive incoming call notifications on MultiLine. The user will not receive incoming call notifications from Microsoft Teams.

When administrators change this setting for an existing user, users will be notified by a pop-up message.

Users can adjust this setting in the MultiLine app. See Control MultiLine ring when using Teams.
Read on to learn how to add the MultiLine Messaging App to Teams
Overview
To use the MultiLine Messaging app, you must first add the MultiLine Messaging App to Teams.
How to add MultiLine Messaging App to Teams
You need to add the MultiLine Messaging app to Microsoft Teams.
- Search "MultiLine" from the Teams application menu and select it.
- Right click the app and click Pin.
Note: Pinning the app makes it easy for you to find and use every day!
You're done!
Click the MultiLine Messages icon whenever you want to use MultiLine Messaging in Teams.
Troubleshooting
Error: "The username or password you entered do not match. Please contact your Administrator."
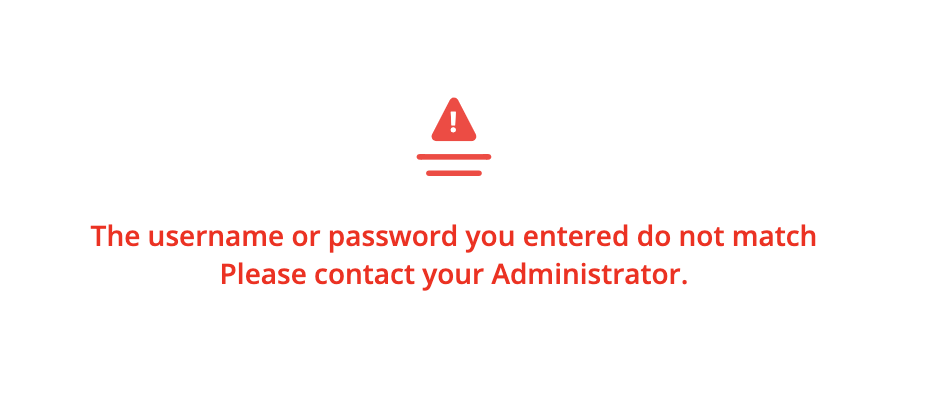
Resolution: MultiLine Messages app requires authentication using the username and password associated with your Exchange account.
If you entered your credentials manually, double-check that you have used your Exchange account credentials and entered everything correctly. If you didn't see a screen to enter your credentials, please contact your IT administrator (not Movius support) There may be an error in the configuration.
Error: "Error logging in. Please contact your Administrator."

Resolution: Contact your IT administrator (not Movius support). There may be an error in the configuration.
Read on to learn about messaging using the MultiLine Messaging App in Microsoft Teams.
Overview
When your organization uses the MultiLine Messaging App in Microsoft Teams, you can message from your MultiLine number in Microsoft Teams.
When you message someone from Teams using the MultiLine Messaging app, they'll see your MultiLine number. If someone texts your MultiLine number, the text will be sent to your MultiLine app and Teams.
Before you Start
- MultiLine Messaging for Microsoft Teams is not available by default; Movius and your IT admins must set up the application on the backend for this to work.
Send a message
The MultiLine Messaging tab is used for messaging.
- Click the MultiLine messages icon
 to access the app.
to access the app. - Click the
 New Message icon.
New Message icon. - If your organization is using WhatsApp messaging, click on the type of message you want to send.
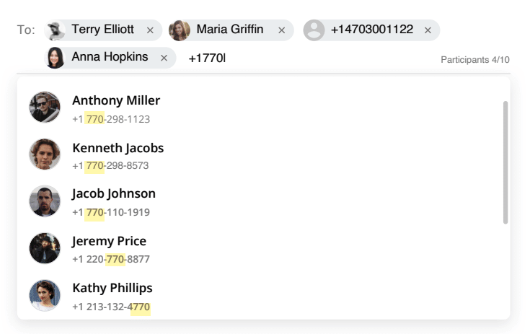
- As you type the name or phone number, a list of matching contacts will appear. Select or add at least one participant.
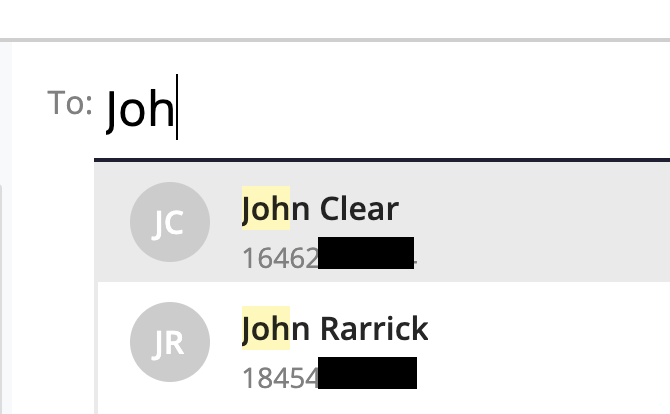
- To create a group message, add multiple participants into the To: field.
- Type your message in the bottom right

- Click
 to select an emoticon
to select an emoticon
- Click
 to send an image file.
to send an image file.
- Click
- Click
 or press 'enter' to send the message
or press 'enter' to send the message
How to receive messages
When you have received a new message you will see a brief notification:
You will also see an Activity notification:


- Either click on any of the notifications, or click the chat directly to open the message thread.
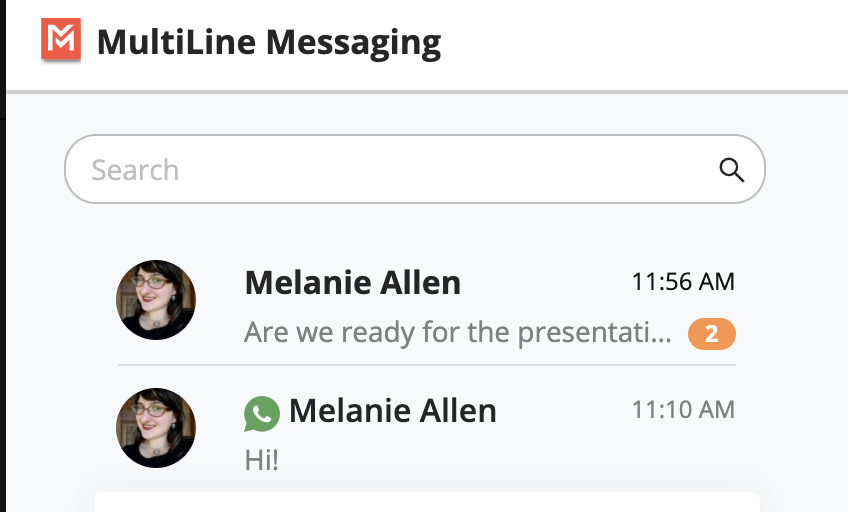
- Orange badges
 represent new unread messages.
represent new unread messages.
Read on to learn about making MultiLine calls in Microsoft Teams.
Overview
If your organization is using MultiLine for Microsoft Teams, you can make and receive calls to your MultiLine number directly within Microsoft Teams.
Before you start
- MultiLine Voice for Microsoft Teams is not available by default; your organization has to set it up for you to use it.
MultiLine Calling in Teams
You'll begin your call using the normal calling feature in Teams. The interface is mostly the same except you will have the MultiLine dialer available.
- Go to the Calls tab.
- Begin typing a name or number into the dialer.
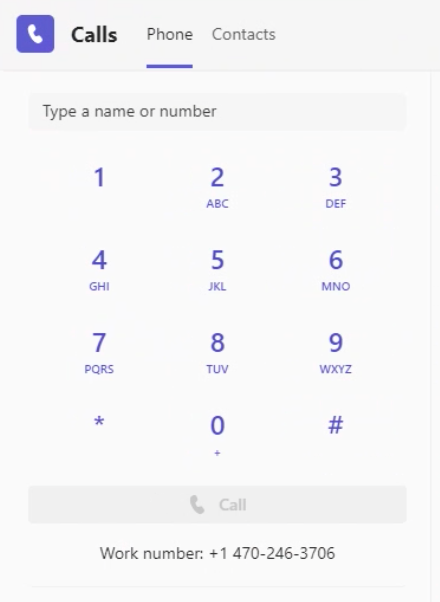
- As you type, matches from your contacts may appear. For more information on adding Contacts in Microsoft Teams, see View or Add Contacts in Teams [External Link].
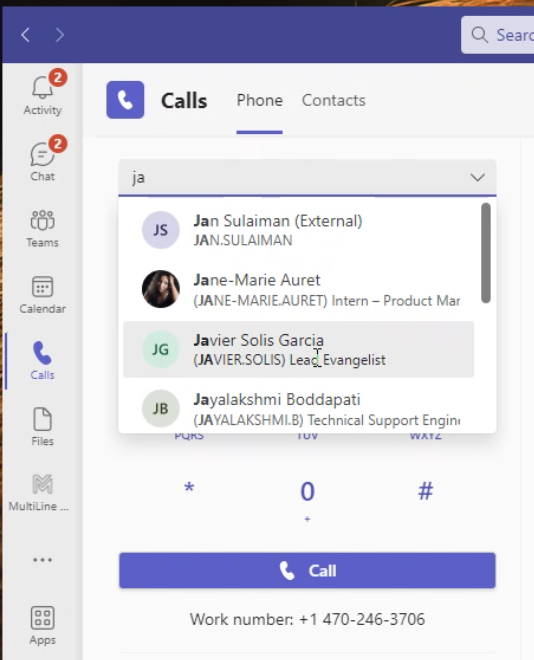
- As you type, matches from your contacts may appear. For more information on adding Contacts in Microsoft Teams, see View or Add Contacts in Teams [External Link].

 will be visible on the toggle and the user will not be able to use Microsoft Teams calling.
will be visible on the toggle and the user will not be able to use Microsoft Teams calling.  will be visible on the toggle and the user will be able to use Microsoft Teams calling.
will be visible on the toggle and the user will be able to use Microsoft Teams calling. to access the app.
to access the app.  New Message icon.
New Message icon.



 to select an emoticon
to select an emoticon
 to send an image file.
to send an image file.  or press 'enter' to send the message
or press 'enter' to send the message
 represent new unread messages.
represent new unread messages.
